A new chat application with ties to a threat actor group known as Gaza Hackers or Molerats, has been used in a long-running cyber espionage campaign in the Middle East, ESET researchers recently announced.
Instrumental in the operation is an Android app, “Welcome Chat,” which serves as spyware while also delivering the promised chatting functionality. The malicious website promoting and distributing the app claims to offer a secure chat platform that is available on the Google Play store.
However, according to ESET researchers, "both those claims are false; the claim of being 'secure' couldn't be further from the truth."
"In addition to Welcome Chat being an espionage tool, its operators left the data harvested from their victims freely available on the internet. And the app was never available on the official Android app store,” said Lukáš Štefanko, the ESET researcher who conducted the analysis of Welcome Chat.
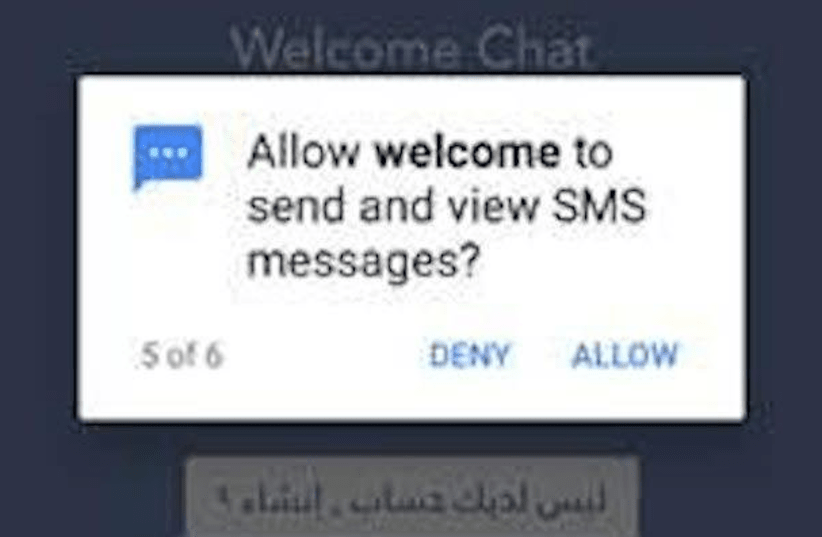
According to the researchers, the Welcome Chat behaves like any other chat app downloaded from Google Play. However, after installation it requests permission to send and view SMS messages, access files, and record audio, as well as requesting access contacts and device location.
"Immediately after receiving the permissions, Welcome Chat starts receiving commands from its Command and Control (C&C) server, and it uploads any harvested information. Besides chat messages, the app steals information such as sent and received SMS messages, history of calls, contact list, photos, phone call recordings and GPS location of the device," the researchers noted.
Additionally, the researchers said that they tried to find out if there was a "clean" version of the app that was being manipulated, or if it was a malicious app developed from scratch.
"We did our best to discover a clean version of this app, to make its developer aware of the vulnerability. But our best guess is that no such app exists. Naturally, we made no effort to reach out to the malicious actors behind the espionage operation,” said Štefanko.
Read more from Cybertech News: https://www.israeldefense.co.il/en/categories/cybertech